Before you proceed with generating Server and Client SSL Certificates, make sure that the Date & Time on the Server is correct
If the Date & Time, or the TimeZone is not correct, either on the Server or the Clients, the generated certificates might not be accepted by the Clients.
Example:
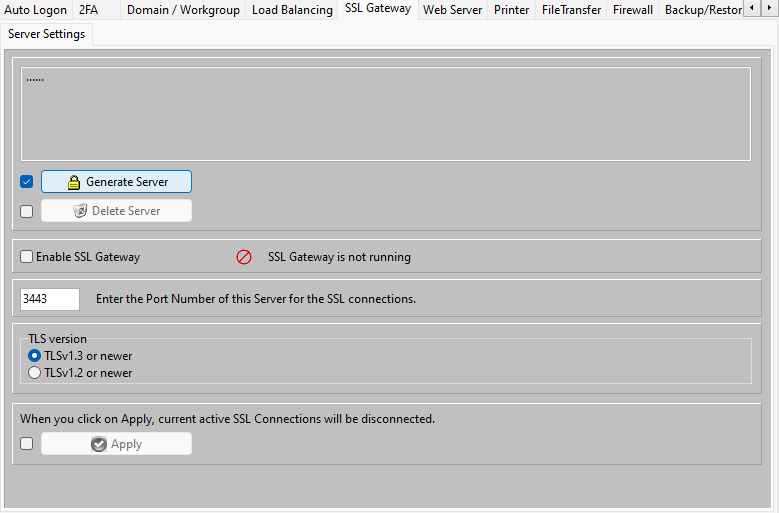
After a fresh installation of AADS Terminal Server, the Terminal Server does not have any certificate. Enable the “Generate Server” button, and you can generate a Server Certificate- Key pair.
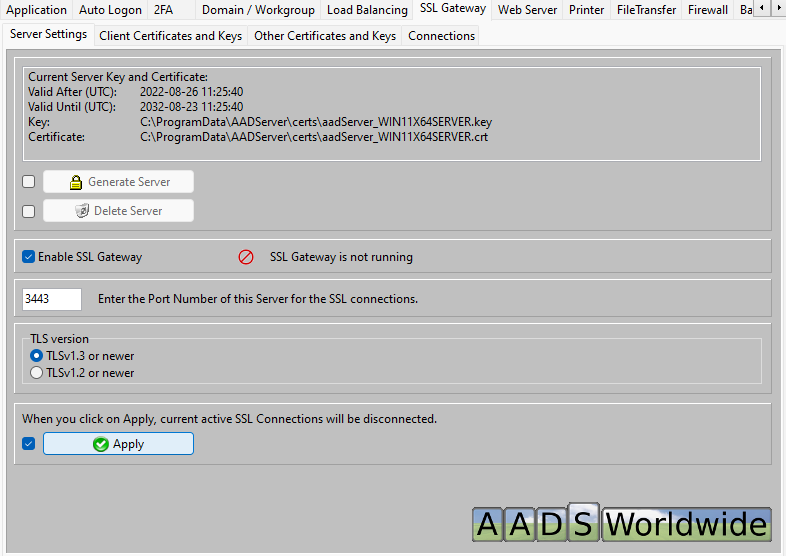
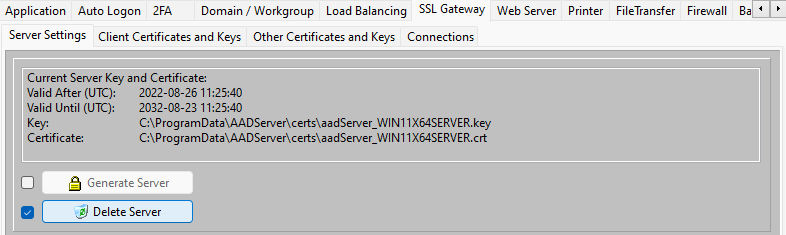
Using the Delete Server button you can delete the current Server Certificate- and Key pair.
The Server Certificate (not the Key) will be made available to the Client. If you Delete the current Server Certificate- and Key pair, and generate a new pair, you will need to distribute a Client Setup Build to all your clients in order to supply them with the new Server Certificate.
After deleting the current Server Certificate- and Key pair, it is not possible any more for any Client who has the current Server Certificate, to establish a connection with the AADS Terminal Server.
Therefore, be careful with deleting the current Server Certificate- and Key pair. Use it only deliberately when you do not want that Clients who knows the current Server Certificate are able to establish a connection with the AADS Terminal Server.
After generating the Server Certificate and key pair, you can start the SSL Gateway:
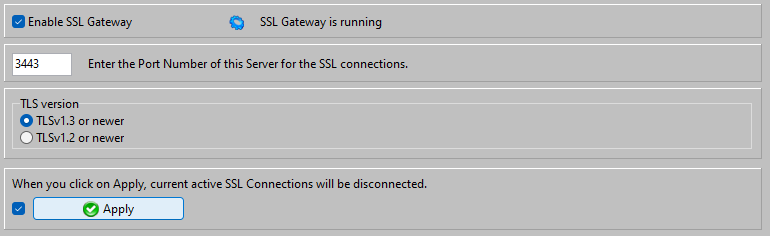

TLSv1.2 as used by AADS is still OK (this manual is dated 1 Sep 2022...)
Currently there are no known attacks against TLSv1.2 which would somehow break the encryption.
However, moving forward with better and stronger encryption is in general a good idea.
 |
Some Users are using Windows XP on the Client PC. The AADS Clients for Windows can be used on Windows XP. However, when running on Windows XP, the AADS Client will use an older SSL-library with "only" TLSv1.2. |
 |
Some Users are using OSX Mojave (10.14) or older. The AADS Client for OSX can be used on OSX Mavericks (10.9) and newer. However, when running on OSX Mojave (10.14) or older, the AADS Client uses an older SSL-library with "only" TLSv1.2. |
 |
Some Users are using an old, ancient Linux distri, or some kind of thin client device with Linux that is not maintained or updated by the manufacturer of the client device. In such a case, the AADS Client for Linux uses an older SSL-library with "only" TLSv1.2. |
|
|
AADS Client Devices |
AADS uses: OpenSSL 1.0.2p |
AADS uses: LibreSSL 3.5.2 |
 |
Windows XP Server 2003 |
√ |
|
 |
Windows Vista and newer Server 2008 and newer |
√ |
|
 |
OSX Mavericks ... OSX Mojave |
√ |
|
 |
OSX Catalina and newer |
√ |
|
 |
"old" Linux distri |
√ |
|
 |
"uptodate" Linux distri |
√ |
If AADS has already been used before, and the SSL Gateway has already been used before,
in this case the Client Devices are currently running older, previous builds of AADS Client software.
Older, previous builds of AADS Client software can "only" do TLSv1.2.
The AADServer has been updated with the latest AADS build, including the ability to do TLSv1.3.
However, it will also be required to update the Client Devices...
Client Devices are automatically updated when the Client Device makes a connection with the AADServer.
However, there will be 1 moment, 1 connection,
where the Client Device is not yet updated, running the current installed older AADS Client software, using TLSv1.2.
This is the 1 moment, the 1 connection, where the AADServer has been updated with the latest AADS build, including the ability to do TLSv1.3,
but where the Client Device has not yet been updated and is therefore doing TLSv1.2.
In this scenario it is desirable that the AADServer accepts and allows for a short period, for example 1 month, TLSv1.2 connections,
such that in this 1 month, each Client Device can connect with TLSv1.2,
can automatically update the AADS Client software,
and the next time the Client Device does connect, the Client Device is running the latest AADS Client software using TLSv1.3.
The 32 bits version of AADS Terminal Server stores the certificates in the folder:
| c:\program files\aadserver\certs |
The 64 bits version of AADS Terminal Server stores the certificates in the folder:
| c:\programdata\aadserver\certs |
All other functionality is identical.
In the logging-folder of an AADS Terminal Server a log file is created which contains logging about failed SSL connections. For example, when a Client Certificate- and Key-pair is deleted, and an user is still attempting to connect to the AADS Terminal Server(s) using this Certificate- and Key-pair, it will logged.
The 32 bits version of AADS Terminal Server stores the logging in the folder:
| c:\program files\aadserver\logging |
The 64 bits version of AADS Terminal Server stores the certificates in the folder:The 64 bits version of AADS Terminal Server stores the certificates in the folder:
| c:\programdata\aadserver\logging |
|
© 2012-2023 AADS WorldWide. Terminal Server | Application Server | Remote Desktop solutions | Firewall |