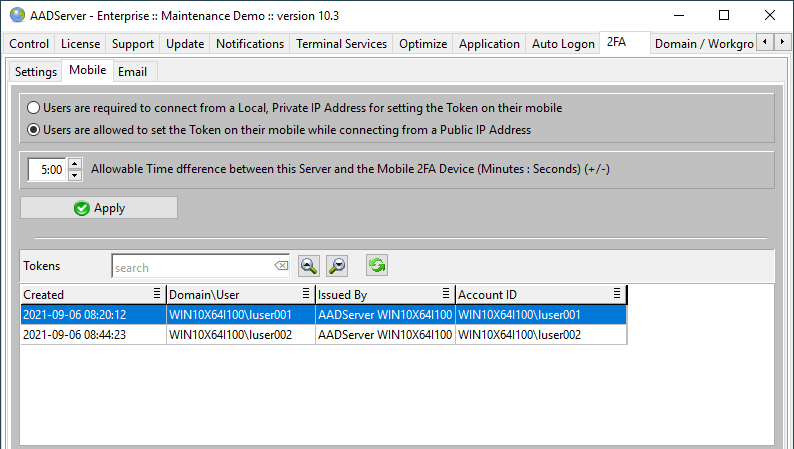
The 1st Time an User does connect to the AADServer, a Mobile Token is generated for the User, and the User is expected to "Save" this Mobile Token on his/her Mobile Device.
In order to avoid that this "1st Time Token Generating" is done by a remote hacker on the Internet, it might be better to require that the User comes to the Office,
assuming that within the Office building Local IP Addresses are used.
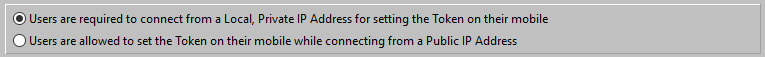
The protocol as used for the OTP is based on the Open Standard RFC 6238. This standard required that both the Server and all Mobile Devices do have correct Clock and TimeZone settings.
A small difference is Time is allowed, and how small this Time Difference is, can be set by the Administrator.
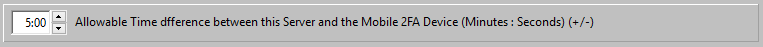
The Tokens as generated are shown. In case this Server is used in an AADS Farm, the Tokens of the other Servers in the Farm are also shown:
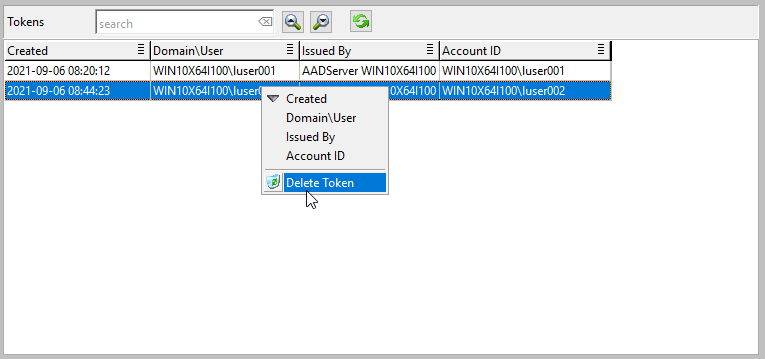
The Administrator can "Delete" Tokens. When a Token is deleted:
The first time an User does connect to the AADServer, the 2FA Mobile Token is generated. This is shown to the User:
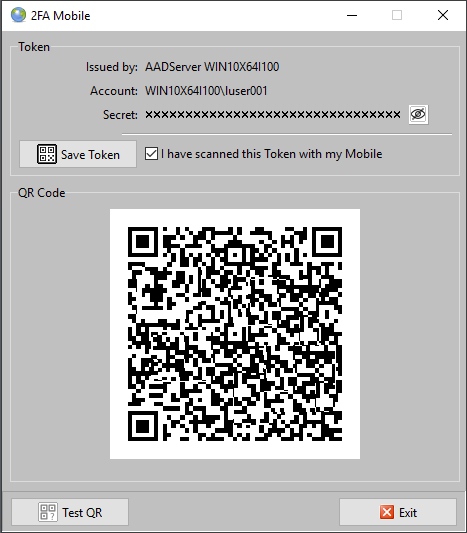
The User is expected to "scan" the QR-code with his/her Mobile Device and "Save" the Token on his/her Mobile Device.
After the user has Saved the Token on the Mobile Device, the session will disconnect.
The User can optional "test" the scanned Token by clicking on Test QR.
A "test-popup" will be shown to the User:
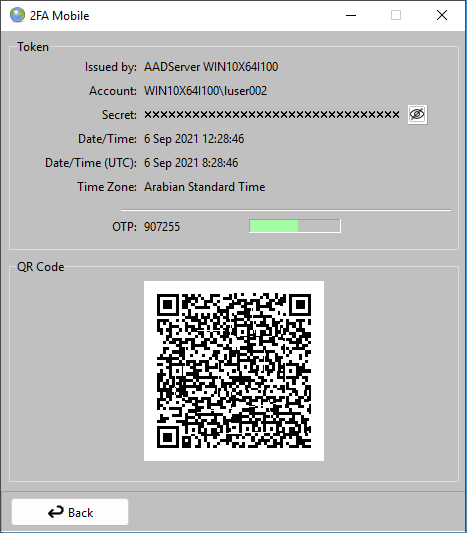
The shown OTP code should match with the OTP code as shown on the Mobile Device.
Both the Local Time and the UTC time of the AADServer is shown, because if the OTP code does not match with the Mobile Device,
most likely the AADServer and / or the Mobile Device do not have correct clock settings.
A small "time difference" between the AADServer and the Mobile Devices is acceptable:
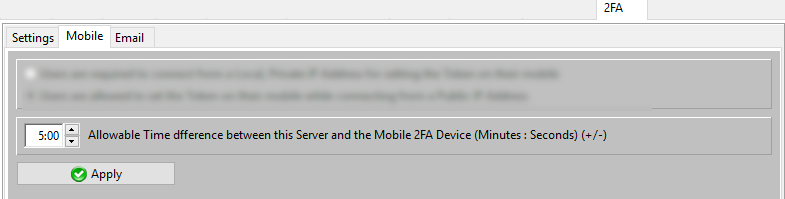
The maximum Allowable Time difference can be set by the Administrator on the AADServer.
The next time the User does a connect to the AADServer, the user is presented with a Dialog where he/she needs to enter the OTP code as it is generated by the OTP App on his/her Mobile Device:
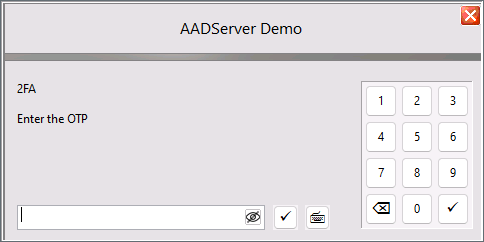
|
© 2012-2023 AADS WorldWide. Terminal Server | Application Server | Remote Desktop solutions | Firewall |