Quote from the Spamhaus website: DROP includes netblocks that are hijacked or leased by professional spam or cyber-crime operations (used for dissemination of malware, trojan downloaders, botnet controllers).
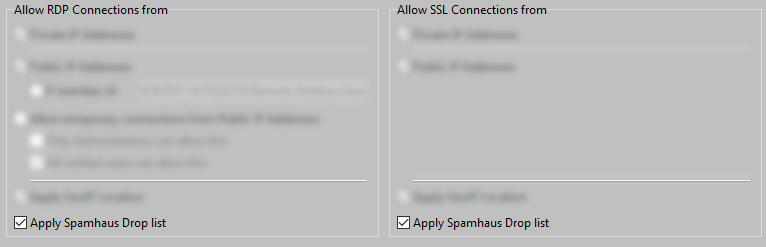
It is unlikely that legitimate users do need to do a login on an AADServer, from one of the netblocks / IP ranges which are included on the Spamhaus Drop list. Therefore it is better to block all connections from these netblocks / IP ranges.
Information and details about the Spamhaus DropList can be found here.
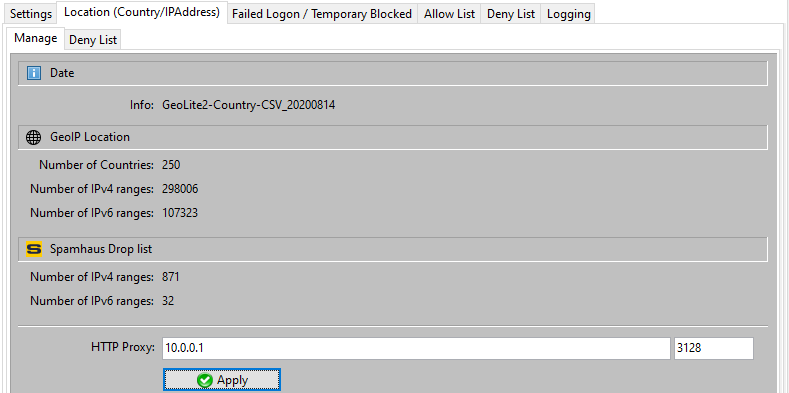
AADS RDP Firewall does filter using the following Spamhaus list:
It is important that the AADServer can check for Updates of the GeoIP location / Spamhaus Drop List, and Download the data.
Both the GeoIP data and the Spamhaus Drop List are updated roughly on a daily to weekly basis and is therefore "outdated" within a month. Using "outdated" data should be avoided because nowadays IPv4 networks are (re-)sold from country to country, implying that "outdated" data would allow connections from IP Addresses, or block connections from IP Addresses, because in the "outdated" GeoIP the IP Address belong to country "XYZ" while currently the IPv4 range is sold and used in country "ABC".
Suggestion: Enable and use Notifications. Whenever an Update is available or there is some problem with downloading the latest GeoIP location / Spamhaus Drop List data, a Notification is send to the Administrator of the AADServer.
|
© 2012-2023 AADS WorldWide. Terminal Server | Application Server | Remote Desktop solutions | Firewall |