Domain Authorization should not be handled by Windows, but by the AADS Terminal Server. We have our own modules for this. By having our own modules for Authorization, AADS Terminal Server is able to do Application Control for Domain Users.
In the example below, the domain is called ipc.w2k3domain.intern. The server running the domain is called w2k3test:
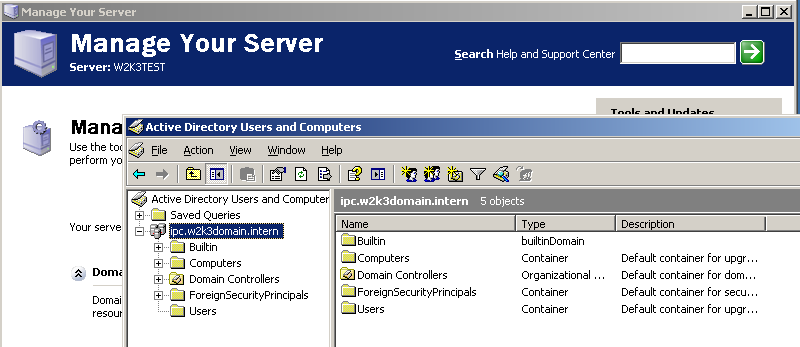
Before you proceed with configuring your AADS Terminal Server, be sure that both the Domain name and the Domain Server name are reachable from the AADS Terminal Server. You can open a DOS-box and use the ping command:
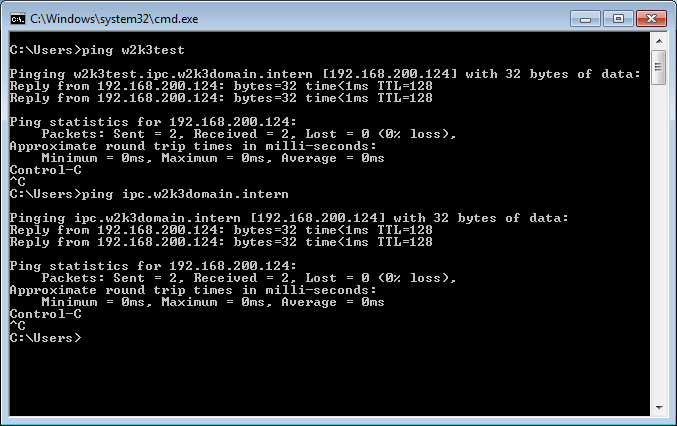
Windows servers do have a so called IPC$ share. The AADS Terminal Server uses the IPC$ on the Domain Server for requests about users. So, be sure that the IPC$ of the Domain server can be accessed by the AADS Terminal Server.
In case you use Samba as a Domain Server, be sure to read the appropriate “howto's” and (online) manuals about Samba. For instance, you will have to define a “netlogon” share in order to mimic a Microsoft Domain Server.
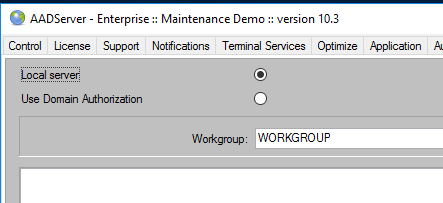
The tab page Domain / Workgroup is the place where you enter the relevant Domain information:
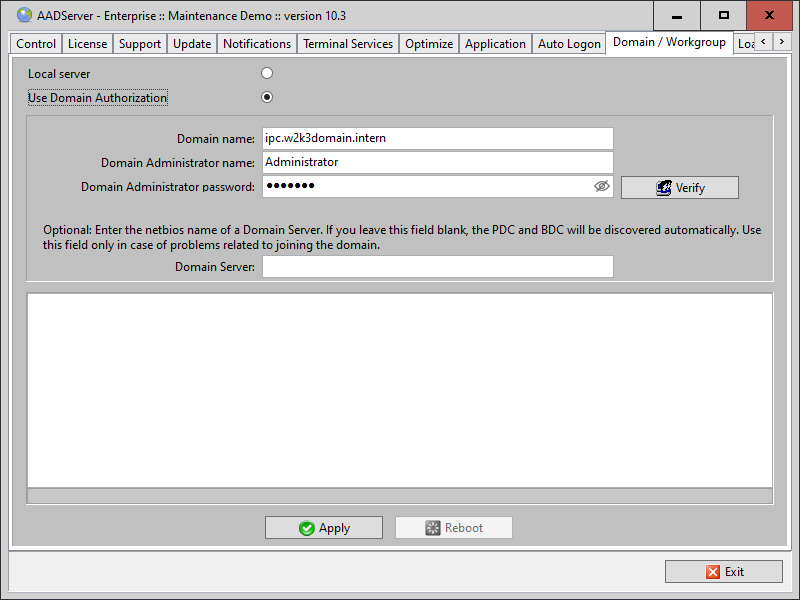
Click on verify, and the entered information will be verified. The progress-logging will be shown.
Click on Apply when done. After clicking on Apply, the Reboot button will be enabled.
It is recommended to reboot the AADS Terminal Server after applying the Domain settings.
The field “Domain Server” is optional. Preferable you should not use it.
In case you do not use the field “Domain Server”, the AADS Terminal Server will automatically determine which PDC and / or BDC is available (Primary Domain Controller and Backup Domain Controller)
If you enter a netbios name of a PDC or of a BDC, the AADS Terminal Server will only use this one PDC/BDC for its domain functions. The AADS Terminal Server will not fallback to another PDC or BDC in case the assigned PDC / BDC is not available.
When the Domain, the network and the AADS Terminal Server are correctly configured, the AADS Terminal Server is always able to determine the Primary Domain Controller (PDC) and the Backup Domain Controller(s) (BDCs).
However, if the network is not configured correctly, the AADS Terminal Server might have a problem:
In this case you can consider to enter a netbios name in the Domain Server field, in order to compensate for the mis-configuration of the network.
When the AADS Terminal Server reboots, it joins the domain. If this does not work correctly, examine the following:
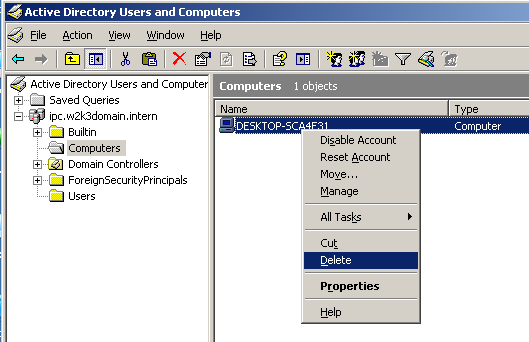
Because the AADServer was deleted from Active Directory, when now joining the AADServer again to the Domain, fresh, new settings will be applied in the Active Directory Administration, and all should be OK.
netbios name TESTW2k3
IP address 192.168.200.210
The PDC does also act as DNS-server
netbios name TESTW2k3b
IP address 192.168.200.211
The BDC does also act as DNS-server
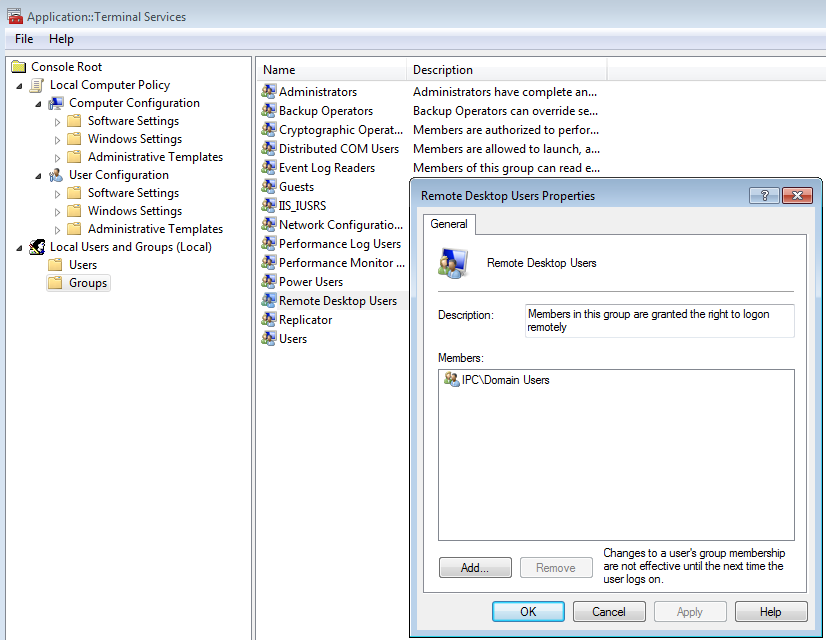
The Domain Group "Domain Users" will be added to the local group Remote Desktop Users by the AADS Terminal Server Setup program:
When it comes to Domain Authorization, AADS Application Control is limited to Domain Groups. It would be possible to include Domain Users, but this might result in performance problems. Large Domains can contain several thousand Domain users. Showing them all and manage them all on an AADS Terminal Server might result in performance problems.
Therefore AADS Application Control can applied only to Domain Groups:
|
© 2012-2023 AADS WorldWide. Terminal Server | Application Server | Remote Desktop solutions | Firewall |